Published: January 31, 2019
We spend lots of time working with our customers on support, user experience, and just general brainstorming. We often see all kinds of brilliant ideas put into action during their investigations, and we always learn a lot from our conversations. From these talks, I noticed there was one mysterious point of data that kept popping up not only in my investigations, but in every one of our customer’s investigations too. Investigations on radically different subjects were united by a single unfamiliar email address.
The solution to this mystery, as it turned out, lay in plain sight all along. A true OSINT mystery story.
Read on.…
While you are browsing around with Hunchly it is extracting the source code (HTML) of the site as well as any available Javascript that it can access when it captures the page.
Hunchly applies some pattern matching to all of that data, looking for things like email addresses, Google Analytics codes, social media account identifiers, and other tasty tidbits that you can pivot off of during an investigation.
This data is presented in the Hunchly Dashboard’s Data tab and page review screen. This is so you can see if there is anything that interests you or generate new investigative leads. We have a lot more in store for this data, so stay tuned for that in future blog posts.
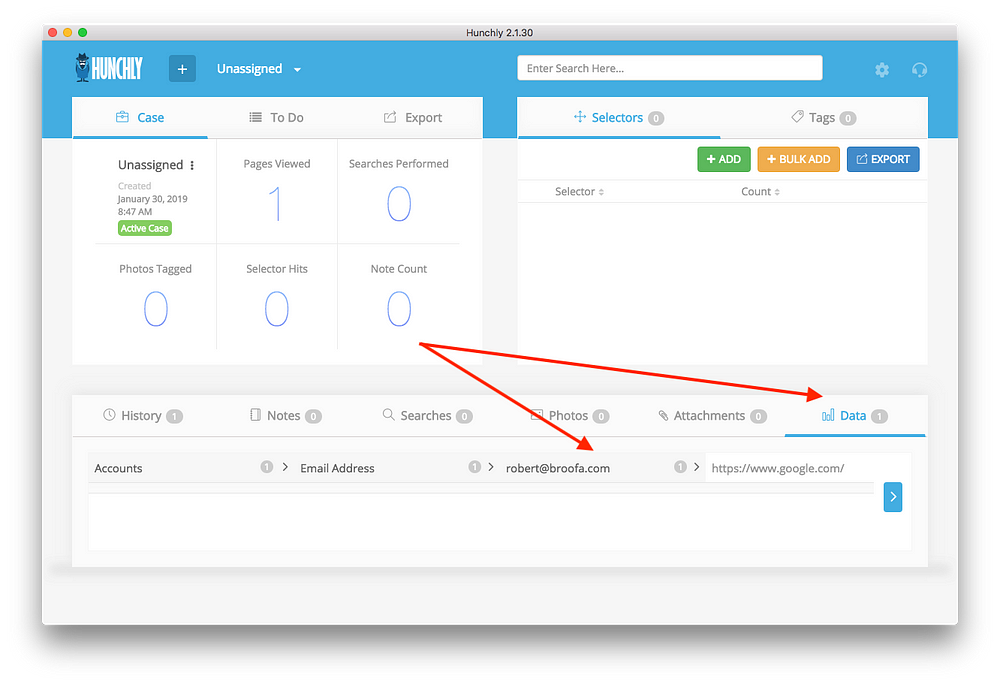
As you can see in the screenshot above, there is an email address that was extracted from Google.com and that email address does not appear to be connected to Google at all.
This had me scratching my head more than a few times as I had seen this data record before. I started asking around, and sure enough, so had the customers I had asked.
Enter stage left: Phil, our intrepid Quality and Support Lead. [Ed. note: he’s also dashing. And good at editing blog posts.]
Phil had access to our development build of Hunchly with an improved page review screen that allows you to hunt through the underlying source code and Javascript. This is a sneak peek of what’s coming in our next release:
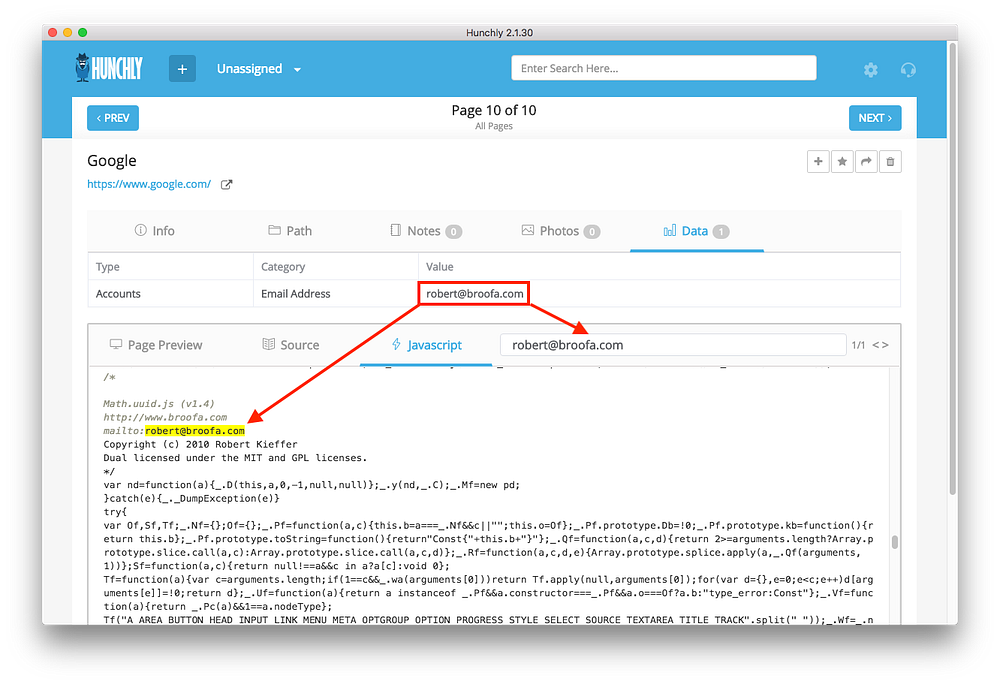
Mystery solved. Robert Kieffer developed the Math.uuid.js library in 2010 which is used in every web search on Google.com. How cool must that be to have a library, with your name on it, used by millions of people every day?
Robert won the open-source lottery and now has the most popular personal email address on the planet.
Well done, Robert. Well done.
(Got another personal email you think is more famous? Let me know on Twitter at @hunchly!)
When I was recently doing a training session for a large group of investigators who use Hunchly, something else unexpected popped out of data extracted from a popular website.
With Hunchly turned on I browsed to a LinkedIn profile and Hunchly extracted a Google Analytics code: UA-62256447–1
An investigator asked me how to demonstrate how this is useful. I showed them how you can leverage tools like Spyonweb, AnalyzeID, PublicWWW and RiskIQ to determine domain co-ownership with analytics codes. If you have multiple domains with the same Google Analytics code there is either co-ownership, or as you’ll see shortly, something else going on.
When I dropped the analytics code into Spyonweb to show the investigators a demo of how this all works, something really weird happened.
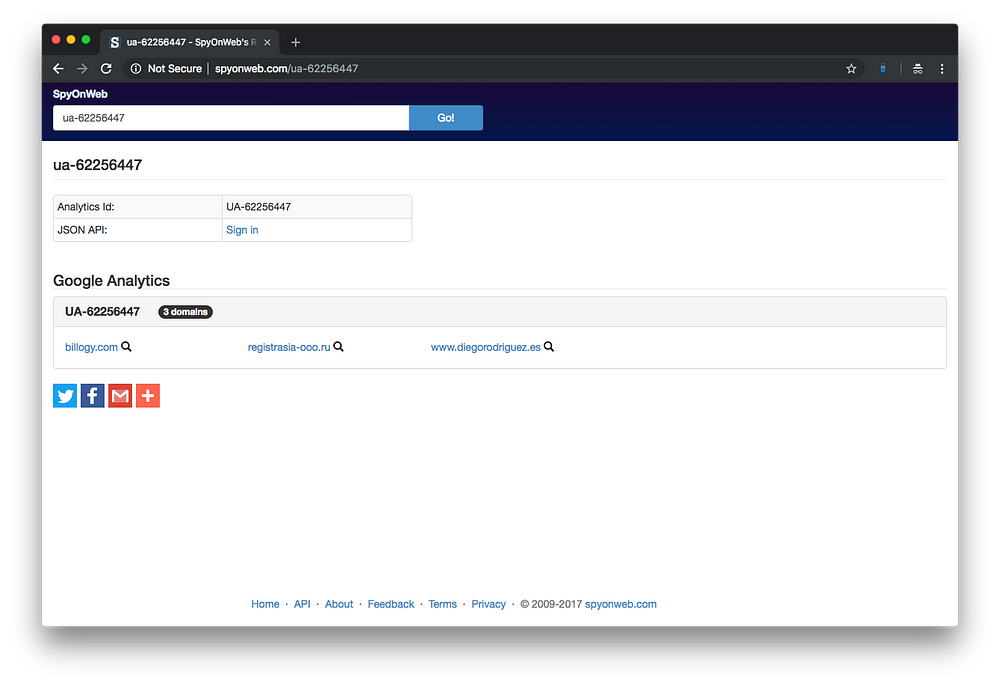
Well that’s a bit weird. None of those sites are LinkedIn.
So being naturally curious I started poking around at the domains above, and I discovered that on March 21, 2018 the Wayback Machine had a record of billogy.com that was a copy of…
You guessed it, the LinkedIn login page.
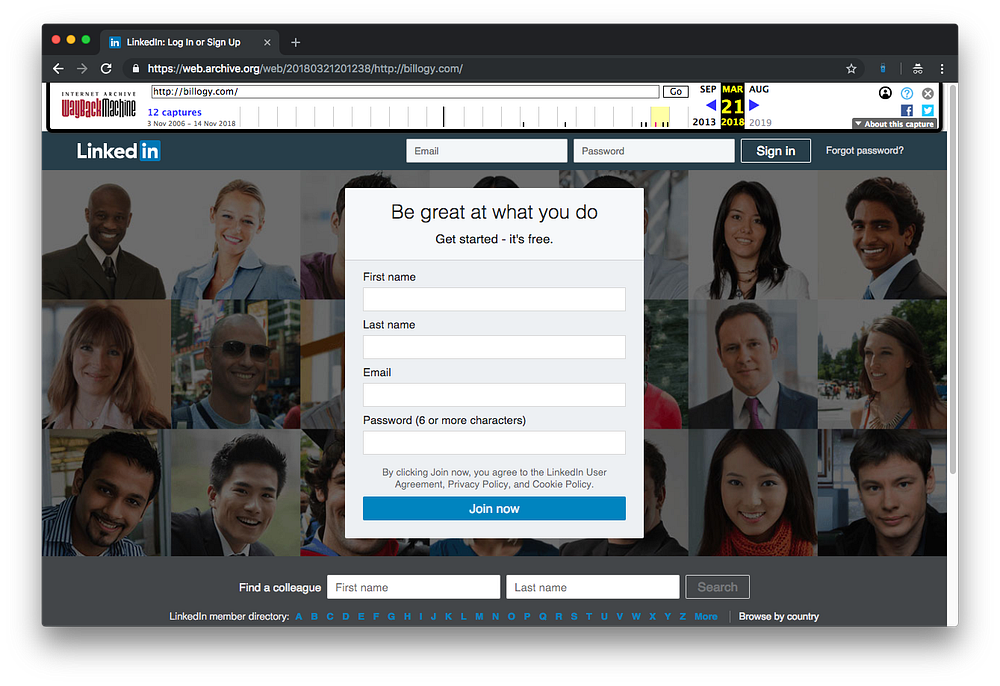
If you use RiskIQ or PublicWWW you can actually find a long list of phishing sites that have just simply copied the LinkedIn login page, including their Google Analytics code with it. This explains why we saw the strange results on Spyweb.
This is actually quite an effective way to determine if a lazy hacker has setup a phishing site for your own domain. Just go search for your own analytics codes and see what results pops up. A little digging on this topic also led me to a research paper that covers some of this as well.
With a little help from Hunchly, we solved some mysteries and found some phishing sites all from a few tidbits of information automatically extracted from two very popular websites.
I’d be really interested to hear of any mysteries you solve using this feature. Drop me a line at: justin@hunch.ly. All war stories welcome.
Justin
